Information is one of the most important organization assets. For an organization, information is valuable and should be appropriately protected. Security is to combine systems, operations and internal controls to ensure integrity and confidentiality of data and operation procedures in an organization. Information security history begins with the history of computer security. It started around year 1980. In 1980, the use of computers has concentrated on computer centres, where the implementation of a computer security focuses on securing physical computing infrastructure that is highly effective organization. Although the openness of the Internet enabled businesses to quickly adopt its technology ecosystem, it also proved to be a great weakness from an information security perspective. The system’s original purpose as a means of collaboration between groups of trusted colleagues is no longer practical because the usage has expanded into millions of frequently anonymous users
Why Information Security
Currently information security is crucial to all organization to protect their information and conducts their business. Information security is defined as the protection of information and the system, and hardware that use, store and transmit that information. Information security performs four important for an organization which is protect the organization’s ability to function, enable the safe operation of applications implemented on the organization’s IT systems, protect the data the organization collect and uses, and lastly is safeguards the technology assets in use at the organization. There are also challenges and risk involves in implemented information security in organization.
Your company’s value is its data
Think you don’t have anything of value to protect? Think again. The key asset that a security program helps to protect is your data — and the value of your business is in its data. You already know this if your company is one of many whose data management is dictated by governmental and other regulations —for example, how you manage customer credit card data. If your data management practices are not already covered by regulations, consider the value of the following:
- Product information, including designs, plans, patent applications, source code, and drawings
- Financial information, including market assessments and your company’s own financial records
- Customer information, including confidential information you hold on behalf of customers or clients
Protecting your data means protecting its confidentiality, integrity, and availability. The consequences of a failure to protect all three of these aspects include business losses, legal liability, and loss of company goodwill. Information security, as a recognised business activity, has come a long way in the past decade. Various factors have caused the discipline to mature and it has now attained its “licence to operate” within the corporate and public sector environments, becoming one of the core business and organisational enablers.
CORE mantra for Information Security:
Security is built – in and not bolt – on
What CORE can help you with
Governance, Risk & Compliance (GRC)
- ISO/NESA Compliance, Audit & Governance
- Operational Risk Management
- Governance framework
- Enterprise Security Strategy
Managed Security Services (MSS)
- VA PT (Remote & Onsite)
- On Demand Mobile Application Security
- Security Device Monitoring
- Real time incident monitoring, response & reporting
Information Security Trainings
- Aspirants workshops for CISSP, CISA, CISM, CoBIT, LA, CRISC
- User awareness trainings (End user, senior mgmt. & tech. staff)
- ISMS related simulation exercises & trainings
- Technical / specialized & Bespoke / customized trainings
- Cyber Security Simulation Game / Exercise
- IRCA ISO27001 LA training
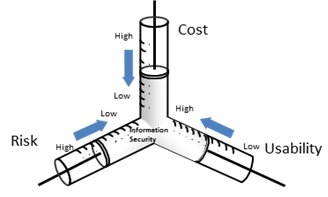
Risks need to be understood – Security Management is the management of Trade-off
Consulting space info@coreconsulting.ae

